Identify, Prevent, and Defend
Cyber Insurance Essentials
As a competitive player in the MSSP space, we offer the services needed for an ideal cyber insurance policy. When it comes to cybersecurity, it's important to understand that tools alone aren’t enough. It takes the right people, process AND tools to hold your own against cybercrime.

EDR + AV
Endpoint Detection & Response (EDR) is an early threat detection software that will remove a compromised device from the the network to prevent further spread.

AI-Driven SPAM Filter
Scans the header & body of an of an email and constantly scanning for known vulnerabilities

Security Awareness Training
Educate your end-users with monthly or quarterly campaigns + simulated phishing attacks and reporting on behavioral patterns
Dark Web Monitoring
Real-time breach detection across the dark web for your business email domains

SOC Services
Security Operations Center (SOC) is a service comprised of a team of people dedicated to monitoring and alerting us of threats on your assets, both physical and in the cloud.

Endpoint MFA & Encryption
Ensure your assets are protected from password hacking & theft with endpoint MFA and encryption
Additional Security Services
Whether you're looking for an assessment to meet regulatory standards set by the Department of Defense for CMMC and NIST 800-171, or operate under HIPAA regulations, we offer flexible compliance services and solutions.
Compliance-as-a-Service (CaaS)
CaaS is the latest service offering within our cybersecurity and compliance-focused solutions.
With CaaS, we can utilize the following features from our tools to give you the transparency you need for regulatory commerce:
- Automated Scans
- Online Forms and Worksheets
- Task Assignment and Notification
- Auditor Checklists
- Scheduled Scans
- Risk Treatment Plans
Key Features of Managed Compliance
| FEATURE | DESCRIPTION | BENEFIT |
| Automated Scans | Technical scans performed by the Compliance Manager software. | Removes human error by using the appliance to collect technical data. |
| Online Forms and Worksheets | Complete worksheets and forms to provide information that isn't obtained through automated scans. | Brings all pertinent network information into a single location that cannot be collected automatically. |
| Augment Data from Automated Scans | Non-generic forms are created using the data collected within your network. | Answer questions about your unique environment, users, and devices for details that cannot be collected automatically. |
| Auditor Checklists |
Summary documents of compliance with cross-references to other documents, including Evidence of Compliance. |
Assesses your compliance position to easily show Auditors how you are going about compliance. |
| Evidence of Compliance | A document that shows detailed information from automated scans, augmented data, and questionnaires. | Keeps information organized in one document to back up the Auditor Checklists with accurate data. |
| Information Policies and Procedures | For organizations that may not have information policies and procedures (P&P) implemented, we provide a standardized P&P that is designed as a starting place. | Since one of the first requirements for regulatory compliance is to have a P&P in place that conforms to compliance standards, we provide one ready to implement into your organization. |
| Scheduled Scans | Performs re-scans on a periodic basis | Looks for when you might need to updated compliance documentation to be current. |
We offer a range of threat management services to protect businesses from cyber threats, including one of the most powerful solutions on the market:
Zero Trust Threat Management
- Application Control: Implement strict access controls and continuous verification for applications across all computers/servers on your network to minimize trust and reduce the attack surface.
- Elevation Control (Privileged Access Management): Users can request elevated permissions on an application they have/need in order to maintain both efficiency and security. Elevations can be created as one-off, time-based policies or as a persistent policy.
- Storage Control: Apply zero trust methodologies to manage and protect data storage, ensuring that access is strictly controlled and monitored, with encryption and segmentation strategies to secure sensitive data.
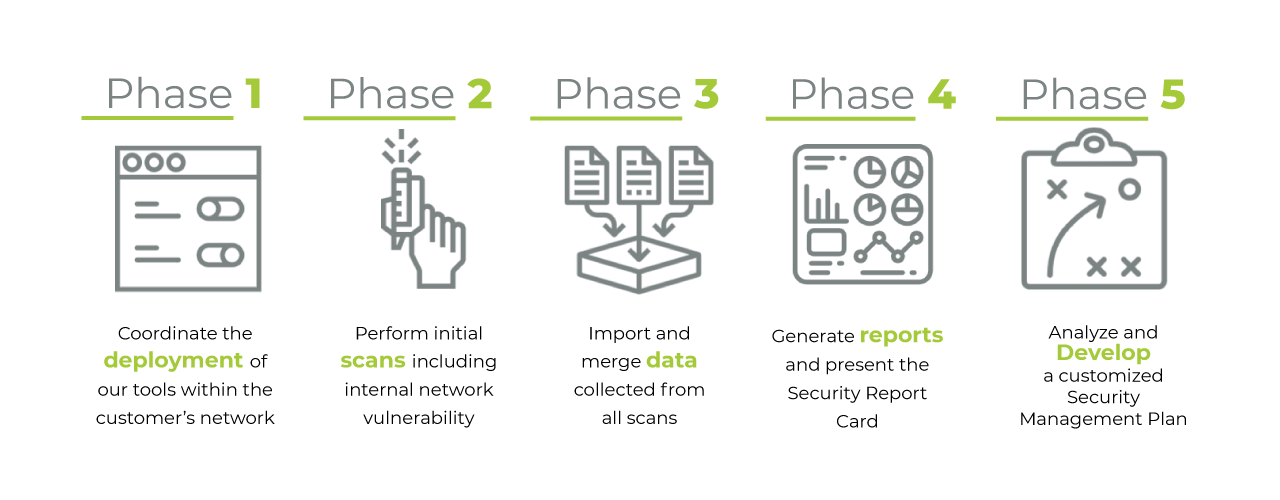
Cybersecurity Assessment Overview
Security for Every Layer of Your Business
Security touches not only software and applications, but every layer of your network infrastructure, vendors, and staff.
Start with a Strategy
Strong security requires a base strategy you can build on as the threat landscape continues to change.
Threats are growing more hostile, budgets have been tightened, and skills remain at a premium. Yet important modern business imperatives like mobility, social media, web applications and big data pose ever increasing risks and inefficiencies if not properly managed.
There are countless configurations you can implement to your infrastructure to get started off on the right foot. Most often, however, the problem isn't starting off with strong protection- it's staying current with industry changes, updates and best practices.
Evolving Cyberthreats Require Evolving Security Standards
Security practices need to be fortified with continuous testing, monitoring and review. Superior Managed IT can help you solve these challenges through our integrated technologies, world-class threat intelligence, and highly flexible managed services tailored to meet the unique needs of your business.
Your Business Needs a Proactive Security Partner
Superior Managed IT has proven compliance and security expertise, sophisticated threat management capabilities, and business-class 24/7 support paired with fully integrated technologies and flexible managed services.
We help our clients get away the "daily firefight" that diverts time and resources away from critical business operations.
We will help you establish an automated, proactive and sustainable data protection, compliance management and business enablement strategy that will save you time and money.

Benefits of Managed Security Services
Software updates, often referred to as patches, are critical releases designed to fix specific security gaps and vulnerabilities that attackers could exploit.
Leveraging centralized vulnerability management solutions, our system routinely implements Microsoft updates and patches, as well as updates for various third-party applications, from a unified control hub on a monthly schedule. This process ensures our network remains secure against emerging threats by keeping all software components up-to-date.
Our role is to empower and guide your team through developing key security policies, recognizing that you understand your operations best.
We act as a specialized resource, guiding you through the intricate process of policy creation. By providing expert insights, templates, and best practice guidelines, we facilitate your team in identifying unique risks and operational requirements. Our collaborative approach ensures that the policies you craft are not only comprehensive and customized but also fully aligned with your business objectives and the latest compliance standards.
By harnessing the combined powers of Security Operations Center (SOC) and Endpoint Detection and Response (EDR) technologies, our cybersecurity framework excels in centralizing threat alerts from both servers and workstations.
This strategic integration empowers us to rapidly pinpoint and neutralize malicious threats before they spread, substantially elevating our security stance and improving our capacity to respond decisively to cyber incidents, thereby safeguarding our digital ecosystem more effectively.
Our managed services offer round-the-clock monitoring and real-time alerts for your network infrastructure. Our dedicated after-hours support team promptly addresses all urgent and critical issues.
As a valued Managed Services client, you gain access to our intuitive Client Portal. This platform enhances your experience by offering advanced ticket management features, including the ability to easily submit, track, and manage support tickets.
Prioritize requests based on severity, view updates in real-time, and communicate directly with our Service Desk team for efficient resolution of issues.
1306 County Rd F West
Suite 200
Minneapolis, MN 55112
Service Desk: 612-788-9233
Sales: 612-999-6200
We're here to help
Ready to secure and streamline your IT?
Contact us today to see how we can help secure the future of your business.