Thanks for visiting our blog!
Be sure to check back frequently for the latest industry news and workplace tips.

In our previous blog post “Phishing: How to Protect Your Business from Email Fraud” we explained what a phishing attack was and some automated prevention measures known as spam filters. In this post we are going to focus on what you, the user, can do to protect yourself and your company from attacks.
Before we can discuss protecting yourself it’s important to understand the basic email structure. Below is an image of your standard email (this is an example pulled from Outlook and may look different in other mail clients). Please not the header and all its parts, where to find attachments, and in the message itself the greeting, body, closing statement, and signature.
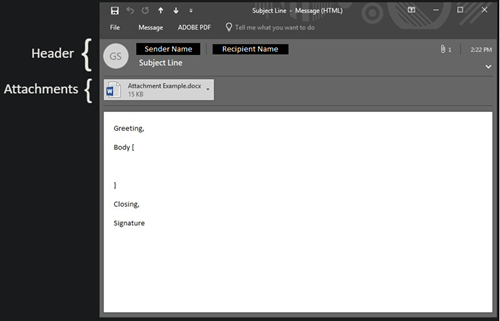
The easiest way to protect yourself and spot a potential threat is to use the 10 second rule before interacting with ANY email (no matter who the sender may be). The 10 second rule is exactly what it sounds like, taking 10 seconds to review the different elements of the email for suspicious content. Below we will explain what you should be looking for when trying to detect a fraudulent email.
The header will contain the email sender, email recipient(s), any CC’d recipients, and a subject line. First examine the sender, and most importantly, their domain. For example, if you were to receive an email from info@superiormanagedit.com, the domain (superiormanagedit.com) can be confirmed as a valid source. However, if you were to receive an email from info@superiormanaged1t.com (notice the spelling difference in the domain) this should cause red flags to jump out at you.
Within the header there is also a subject line. In the subject line you should be suspicious of any dramatic or threatening language that may be trying to persuade you to act.
The simple rule for attachments is look, but don’t touch. Until the remainder of the email has been cleared by your inquisitive eyes there’s no reason to open an attachment. Even after you have determined that the email has come from a legitimate source, if the attachment is of a file type that you do not recognize or named in a suspicious manner it is best to inform your IT team and have them review before opening.
This is the meat of the message, where the sender is expressing themselves to you, the recipient. Much like in the signature line it is important to be wary of any dramatic or threatening language that tries to create a sense of need to act. Along with being wary of the language also take note of any direct requests for personal information, especially banking information or passwords.
Within this section of an email a sender can also conceal links both the standard text but also in any images (often found in the signature line). Like attachments the simple rule for a link is look, but don’t touch. The true destination of a link can be hidden from sight, by hovering your mouse over the link it will provide you with the true address of the link. Use the same rules for inspecting the sender’s domain to inspect the true link domain.
If you ever find yourself asking this question, even if it’s just the smallest of whispers in the back of your mind, the best thing you can do is reach out to your IT department. No email, no client, no threat of account closure or suspension is ever worth the risk of responding too if it could put yourself or your company in at risk.
1306 County Rd F West
Suite 200
Minneapolis, MN 55112
Service Desk: 612-788-9233
Sales: 612-999-6200
We're here to help
Contact us today to see how we can help secure the future of your business.