Phishing Attacks In our previous blog post “Phishing: How to Protect Your Business from Email Fraud” we explained what a phishing attack was and some automated prevention measures known as spam filters. In this post we are going to focus on what you, the user, can do to protect yourself and your co ...
The Superior Managed IT Blog

Top 10 Windows Keyboard Shortcuts: Efficiency at the Press of a Key
Windows provides a way of quickly accessing some of its most useful functions. These include locking your user account, starting Task Manager, opening File Explorer, and many others. All these tasks have been assigned a specific combination of keys, which when pressed simultaneously, will perform the task immediately.
Microsoft SharePoint
What is Microsoft SharePoint? SharePoint is Microsoft’s “intranet” platform, allowing users to “Share and manage content, knowledge, and applications to empower teamwork, quickly find information, and seamlessly collaborate across the organization.” (Microsoft, 2019) Whether you’re updating a comp ...

Windows 7 End of Life is Around the Corner
Are you one of the 40.1% of users who still have a Windows 7 Operating System?
Microsoft released a bulletin announcing End of Life support for Windows 7.
End of Life Means End of Support
After January 14, 2020, security updates and support for Windows 7 PCs will no longer be available.
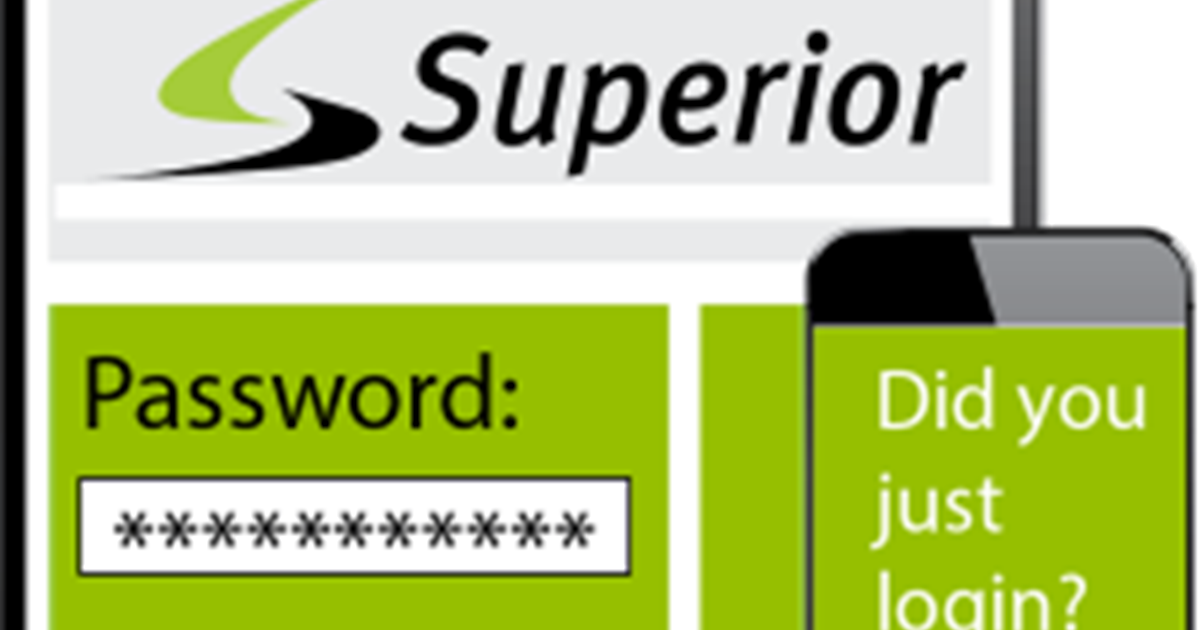
Multi-Factor Authentication
Keeping on the topic of e-mail security from last month’s post, another great way to secure your e-mails is by setting up Multi-Factor Authentication (MFA) for your accounts.

Phishing: How to Protect Your Business from Email Fraud
For all the productivity-boosting qualities it holds, email has transformed business communication in ways that are not all for the better.
Email hacking is incredibly common, and one of the most successful tactics used by hackers is known as phishing.
1306 County Rd F West
Suite 200
Minneapolis, MN 55112
Service Desk: 612-788-9233
Sales: 612-999-6200
We're here to help
Ready to secure and streamline your IT?
Contact us today to see how we can help secure the future of your business.
