Erin joined the SMIT Team in 2017. Her passion for technology and commitment to helping others inspired her career transition from Transportation Safety & Compliance to IT.
The Importance of a Strong Data Governance Policy

Modern File Sharing Challenges
Internal & external file sharing and collaboration solutions have been in high demand for years, and with the world looking diligently for optimized remote-worker solutions, the need has spiked dramatically across businesses around the world.
The beauty of modern file sharing and collaboration is that it’s fast, if not instant, and can be configured with tight security restrictions (or from what we see all too often, none at all). The part of file sharing that is often overlooked is communicating to staff about your expectations as a company. The reason this pivotal step is missed is because it is a new concept for a lot of companies who probably haven’t heard of a data governance policy, and therefore wouldn't know to have one in place.
Protecting Your Sensitive Data & Intellectual Property
Creating a data governance policy will help educate your staff on why certain restrictions and guidelines are in place. If you have contractual obligations with the Department of Defense (DoD), for instance, your staff are probably well-versed in what data is considered “sensitive” and therefore shouldn’t be shared. However, your intellectual property (IP) isn’t always safe-guarded as strictly as a military-regulated requirement, and is more than likely being shared across email and your internal messaging platforms like Microsoft Teams, Slack, RingCentral, Zoom.
Take a moment to think about what valuable information could be intercepted if an employee, recipient, or you fell victim to a phishing or spoofing attack.
Malicious Data Breaches
Often times, these communication platforms are cloud-hosted, and not protected by encryption or MFA (Multi-Factor Authentication), which make them increasingly vulnerable to hackers. The second an account on your network is compromised, you have an unintentional data leak.
Internal Data Breaches
At Superior Managed IT, we recognize that not all breaches are malicious. The lines of access and security permissions and can become blurred when using file sharing in messaging platforms. Individuals in your company may share documents that they weren’t aware was only accessible to them based on permissions assigned to them in Active Directory on your server. Your data governance policy should include clearly expectations for internal file sharing to reduce ambiguity and set your staff up for success.
Data Governance Models
An important first step to defining a data governance policy is understanding which model your organization best fits into. This will give you better insight into the best practices for your type of business.
The 4 data governance models are as follows:
- Decentralized Execution for Individual
- Decentralized Execution for Team
- Centralized Governance
- Centralized Data Governance and Decentralized Execution
Decentralized Execution for Individual
Classification
This model is characterized by individual users who are tasked with creating, maintaining and typically consuming their own master data. Think of these individuals as the department heads in a small business.
Special Considerations for this Model:
- Flat structure with individual accountability
- No shared master data with other business units
- Data maintenance is simplified

Image Source: IntelligenceGroup
Decentralized Execution for Team
Classification
This data governance model is characterized by user teams maintaining their own master data. Teams work together on shared customer, material and vendor data.
Special Considerations for this Model:
- No data governance owner
- The more parties involved, the higher probability of experiencing inconsistent data
- duplicate master data
- inconsistent data resulting in inconsistent or meaningless reporting

Image Source: IntelligenceGroup
Centralized Governance
Classification
This third data governance model is characterized by operating with master data shared between one or multiple business entities. In this model, one central organization (owner or appointed committee) owns the construction of the master data based on requests coming in from those consuming it.
Special Considerations for this Model:
- Exhibits a high level of master data control
- Master data gets distributed to various systems consistently and more accurately
- Delays can occur in setting up the master data

Image Source: IntelligenceGroup
Centralized Data Governance and Decentralized Execution
Classification
This last model is characterized by a centralized data governance body (owner, or appointed committee) defining the structure and access controls, and individuals/teams responsible for contributing their individual parts of master data.
Special Considerations for this Model:
- Data must have proper controls in place
- Master data gets distributed to various systems
- Allows shared master data between business entities under the same data governance organization
- Compliance will likely be a factor if required to adhere to various regulations
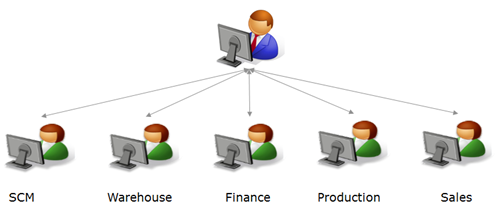
Image Source: IntelligenceGroup
Seek Out an Expert Opinion
There are many resources online that can help you define a strong data governance policy, but a policy isn’t worth much until you have a full understanding of what’s going on in your organization as it stands today.
Before you begin fine-tuning your data governance policy, we recommend working with experts in the field, like our team at Superior Managed IT, to identify potential or existing vulnerabilities. Our network discovery, assessment, and monitoring tools will provide you with a unique insight into your current file structure and user access controls on your network. With this information, you can plan on how to tighten up your security and data governance for a smooth transition into the cloud to use those communication platforms with peace of mind
Contact us today to learn more about how we can help you stay in control over your intellectual property and sensitive data.
Sources:
IntelligenceGroup
1306 County Rd F West
Suite 200
Minneapolis, MN 55112
Service Desk: 612-788-9233
Sales: 612-999-6200
We're here to help
Ready to secure and streamline your IT?
Contact us today to see how we can help secure the future of your business.
