Emerging SD-WAN Technology Has Hit the Market Fortinet announced the release of the first ever SD-WAN appliance for operational technology (OT) environments: FortiGate Rugged 60F. Software-defined wide-area networking (SD-WAN) has been growing rapidly on the corporate side of many organizations. ...
The Superior Managed IT Blog

How to Prepare for Cyberattacks as a Growing Business Interruption
Businesses prepare for downtime from natural disasters with network devices like a UPS (uninterruptible power supply) for unexpected power outages, cloud backups for recovering on-premises data lost in a fire, etc. Which then raises the question: how are businesses preparing for a malicious disaster? Find out how you can prepare for a cyberattack to minimize downtime and interruptions.
SD-WAN: What is it and Why is it Changing Business Networking?
SD-WAN is a new technology with a board range of offerings and varying designs. It allows IT to tackle daily challenges with one network implementation. With SD-WAN, networks can deliver routing efficiently, protect itself from threats, offload expensive circuits efficiently, and simplify WAN network management.

The Importance of a Strong Data Governance Policy
Did you know your data is more vulnerable now than ever before? Learn how you can minimize risks on your business's file sharing platforms. You'll understand the reasons why producing a data governance policy for your business can help you protect your intellectual property and sensitive data.

Tips to Stay Connected with Your Staff Remotely
In wake of COVID-19's impact on local and national businesses, we've been seeing a lot of requests for team collaboration solutions using modern technology to host video meetings, and easily collaborate with chat/instant messaging software. Find out our top recommendations here!

Tips for Enhancing Your Home Network Security
If you are still using the out-of-the-box settings for your home network, you could already be, or easily become compromised. The good thing is, you can factory-reset your home network router, but then what’s next?

Identifying Threats in Your Mailbox
Phishing Attacks In our previous blog post “Phishing: How to Protect Your Business from Email Fraud” we explained what a phishing attack was and some automated prevention measures known as spam filters. In this post we are going to focus on what you, the user, can do to protect yourself and your co ...

Top 10 Windows Keyboard Shortcuts: Efficiency at the Press of a Key
Windows provides a way of quickly accessing some of its most useful functions. These include locking your user account, starting Task Manager, opening File Explorer, and many others. All these tasks have been assigned a specific combination of keys, which when pressed simultaneously, will perform the task immediately.
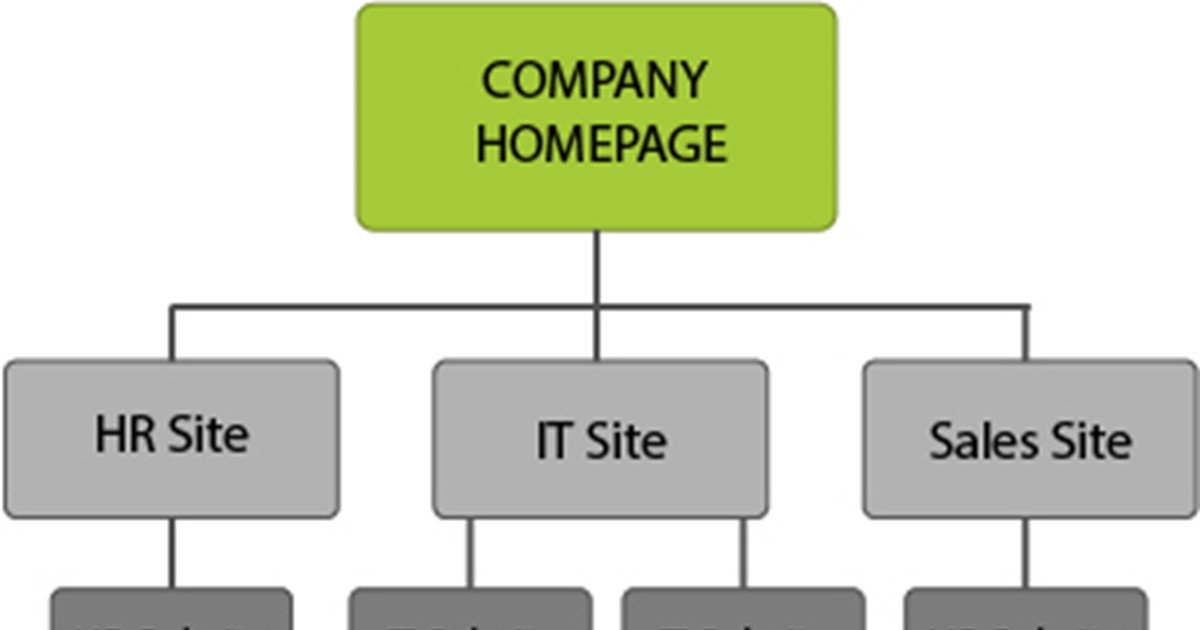
Microsoft SharePoint
What is Microsoft SharePoint? SharePoint is Microsoft’s “intranet” platform, allowing users to “Share and manage content, knowledge, and applications to empower teamwork, quickly find information, and seamlessly collaborate across the organization.” (Microsoft, 2019) Whether you’re updating a comp ...

Windows 7 End of Life is Around the Corner
Are you one of the 40.1% of users who still have a Windows 7 Operating System?
Microsoft released a bulletin announcing End of Life support for Windows 7.
End of Life Means End of Support
After January 14, 2020, security updates and support for Windows 7 PCs will no longer be available.
1306 County Rd F West
Suite 200
Minneapolis, MN 55112
Service Desk: 612-788-9233
Sales: 612-999-6200
We're here to help
Ready to secure and streamline your IT?
Contact us today to see how we can help secure the future of your business.
